SSRF — Server-Side Request Forgery (When converting the HTML file or URL to PDF)

Note: There are multiple ways to find the SSRF vulnerability; here we are choosing the one that is HTML to PDF conversion. You can try it in URL parameters, Webhooks, API endpoints, etc. The following subjects receive all of the article’s attention:
- What is SSRF?
- Requirements to find and exploit the SSRF Vulnerability
- Parameters used to test the SSRF vulnerability
- How to find SSRF?
- How to change the severity (Leads to RCE)?
- Impact of SSRF
- How to prevent SSRF from attacker?
- Conclusion
What is SSRF?
Server-Side Request Forgery (SSRF) is a type of web vulnerability that enables attackers to use a targeted server to send unauthorized requests to other servers and applications, often bypassing firewalls or accessing sensitive data. Successful SSRF attacks can lead to data theft, malware infections, remote code execution, and even server hijackings. To protect against SSRF, security experts recommend implementing strict input validation, using trusted APIs, firewalling, network segmentation, and monitoring for unusual traffic patterns. Regular vulnerability testing and patching can also help to prevent and mitigate SSRF risks (We will see it later in prevention topic).
Requirements to find and exploit the SSRF Vulnerability
Various tools can be used to find and exploit this vulnerability; here we will focus on the manual process and you can also check CVE-2021–40438 is a critical Server Side Request Forgery (SSRF) vulnerability that affects Apache HTTP Server version 2.4. 48 and earlier. If a specially crafted request URI path is used, it can trigger mod_proxy to forward the request to an origin server chosen by the remote user.
The following three are used in this article to find the SSRF:
- Burp collaborator client
- Netcat
- Ngrok
Burp collaborator client:
The Burp Collaborator client is a tool used to facilitate communication between web applications and a testing environment. It works by setting up a unique server that can be accessed through a generated URL. When a targeted application makes a request to the server, the client records the data and sends it back to the testing environment for analysis. This allows testers to identify potential vulnerabilities in the application’s communication with outside servers and ensure that sensitive information is not being exposed. The Burp Collaborator client is a useful tool for testing the security and functionality of web applications.
Netcat:
Netcat, also known as “nc”, is a command-line utility used for networking and security purposes in Linux, Unix, and Windows operating systems. It can be used to send and receive data across network connections, perform port scanning, and establish a backdoor for remote access. Netcat is a versatile tool that can be used for both benign and malicious purposes. It is often referred to as the “Swiss Army Knife” of networking due to its wide range of features. Netcat is primarily used by network administrators and security professionals for testing and troubleshooting network connections and protocols.
Ngrok:
The ngrok is a tool that allows developers to expose a local web server to the internet. It creates a secure tunnel between a local machine and the ngrok servers and then exposes that tunnel through a publicly accessible URL. This enables developers to test and demo web applications without having to deploy them to a public server. Additionally, ngrok provides features such as custom subdomains, TLS encryption, and password protection to make testing and sharing web applications easier and more secure.
Parameters used to test the SSRF vulnerability
The parameters used to test the Server-Side Request Forgery (SSRF) vulnerability include URL inputs, webhooks, API endpoints, FTP connections, and DNS requests. Various techniques, such as changing the URL to a different IP address, using a local IP address or localhost, and inputting malicious payloads, can be used to exploit the vulnerability. Additionally, testing the application’s ability to access internal network resources or sensitive information can also help identify SSRF vulnerabilities. It is crucial to test and mitigate SSRF vulnerabilities to prevent unauthorized access or attacks on a web application or server.
How to find SSRF?
For hunting the SSRF, you need to choose the domain first (here we use Google Dork to find the HTML to PDF converter websites).
- intitle:”html to pdf”
Use the above dork to find the HTML to PDF converter sites, if you want to change the site TLDs from .com to some other TLDs like .in or .org etc., Use this dork
- intitle:”html to pdf” site:*.in
The above-mentioned dork will filter the .in sites for you by ranking them first.
After choosing the domain, just visit the site and check the input field or upload button. If the website is asking you to enter the URL or HTML file to upload, then try this.

For testing the SSRF vulnerability, you need Burp Collaborator Client or Netcat, and ngrok will see both one by one.
Using the Burp Collaborator Client:
Open the burpsuite and go to the burp collaborator client tab and edit the poll every 60 seconds (this will automatically poll every 60 seconds; if you want the response manually, click the poll now button) to 1 second to get the response soon, and copy the URL from the copy to clipboard button under the generate collaborator payload.
To see the external server interaction, just enter the URL in the input field, click the convert URL to PDF button, and see the burp collaborator client for the response. If the burp collaborator receives the DNS and HTTP from the server, it’s vulnerable to the SSRF.

Note: External Service Interaction arises when it is possible for an attacker to induce an application to interact with an arbitrary external service such as DNS, HTTP, etc. External Service Interaction can be limited to HTTP, HTTPS, or DNS; it can also lead to FTP, SMTP, etc. Such weakness can lead to a DDoS attack. External Service interactions can lead to OS Command Injection, DOS attacks, DDOS attacks, or Code Manipulation.
By using netcat and ngrok to find SSRF vulnerabilities,
First, open the terminal and type the following comment:
- nc -nlvp {PORT} — in the port argument, enter the port that you want to listen to.
- Open another terminal or split the terminal and type the ngrok command to generate the URL ./ngrok http 7734 and hit enter (the port number should be the same as the netcat listener).
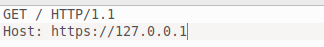
- Then go to the webpage and paste the URL generated through Ngrok in the input field and click the convert URL to PDF button. Then see the response in the terminal to which you are listening.
- You will get the internal server IP address in the X-Forwarded-For header. The response will look like this:

By using the IP address, you can do some information gathering like OS detection, Server detection, open ports detection, nslookup, host detection, etc. Below, I have attached the NMAP result.

You can also try various vulnerabilities with SSRF, for example:
- XXE with SSRF

- Host header injection
- HTML Injection

Impact of SSRF
Server-Side Request Forgery (SSRF) attacks can have a devastating impact on web applications as they allow attackers to interact with internal systems that are usually hidden from public view. Attackers can use this technique to steal sensitive data, compromise internal systems, and launch further attacks on the application or network.
SSRF attacks are notoriously difficult to detect and prevent, often requiring a combination of security controls such as input validation, access controls, and network segmentation. Therefore, organizations should ensure that they implement comprehensive security measures to protect their web applications from SSRF attacks.
How to prevent SSRF from attacker
SSRF (Server-Side Request Forgery) attacks can be prevented by implementing proper input validation and access controls. Applications should only allow access to trusted external resources and should not rely on user input for defining URLs or network configurations. Developers should also avoid using insecure protocols like file:// or allowing arbitrary IP addresses or ports in requests. Server configurations should be hardened and network segmentation can also be utilized to limit the attack surface. Regular security assessments and vulnerability scanning can also help in identifying and remedying potential SSRF vulnerabilities.
Conclusion:
In conclusion, Server Side Request Forgery (SSRF) is a vulnerability that can be exploited by cybercriminals to gain unauthorized access to sensitive data or internal network resources. It is essential for organizations to address this threat by implementing proper security measures, such as input validation and restricting network access. Additionally, consistent awareness and training of employees can help prevent SSRF attacks. To prevent such types of attacks, allow only the particular subdomains of the required web page and then whitelist the other web pages that are not in use. As cyber threats continue to evolve, it is crucial to stay vigilant and proactive in protecting against them.
Always THINK OUTSIDE THE BOX to learn new things!








